As cloud computing adoption continues to surge, businesses must prioritize cloud security to protect critical data and operations effectively.
In 2026, the cloud landscape has matured, but threats are more sophisticated and dynamic than ever before in history.
Organizations face increasing pressure to maintain compliance, secure infrastructure, and protect sensitive information in multi-cloud and hybrid environments. Data breaches, ransomware, and insider threats now impact enterprises and small businesses alike, resulting in devastating operational and financial losses.
This blog explores the top cloud security risks in 2026, along with proactive solutions every organization should implement today.
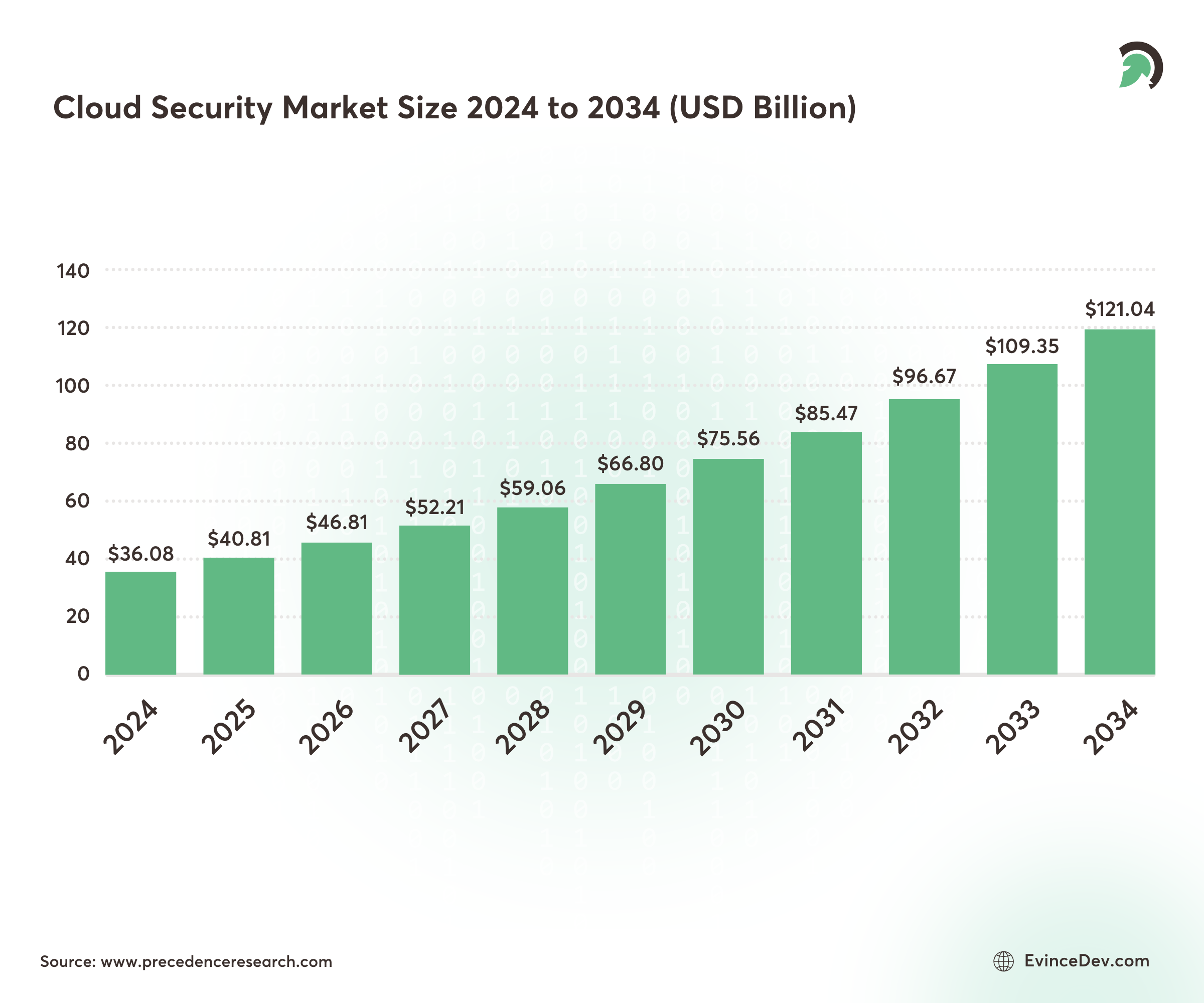
In 2024, cloud security was a USD 36.08 billion global market. It’s expected to climb to USD 121.04 billion by 2034, growing at an annual rate of 12.87% between 2025 and 2034.
Cloud Risk Management: Addressing Key Security Challenges
Discover the most pressing cloud security risks facing businesses in 2026 and explore practical solutions to mitigate threats, ensure compliance, and protect critical data.
Misconfiguration of Cloud Settings
Cloud misconfigurations remain a leading cause of security breaches, often caused by human error or rushed deployment practices. Overly permissive IAM policies or open cloud storage buckets can expose critical company data publicly.
Solutions:
- Use Cloud Security Posture Management (CSPM) tools to detect and fix misconfigurations across cloud environments automatically.
- Enforce security-by-default templates and restrict manual changes in production environments using approval workflows.
- Conduct regular audits of access policies, storage permissions, and service configurations to identify potential exposure.
Insecure APIs & Interfaces
Public-facing APIs are essential for cloud services but represent one of the most exploited attack vectors in modern cyberattacks. Poorly secured APIs can expose backend systems, bypass traditional defenses, and allow attackers unauthorized access to sensitive data.
Solutions:
- Secure all APIs with OAuth2, enforce token expiration, and use encrypted communication for all data exchange.
- Implement API gateways to manage traffic throttling, authentication, and payload inspection across all cloud endpoints.
- Perform routine penetration tests on APIs and use automated API security tools to detect potential vulnerabilities.
Data Breaches & Loss of Sensitive Data
Cloud storage may appear secure, but unencrypted or poorly managed data is vulnerable to breaches, theft, or accidental loss. Sensitive information such as financial records or personal data can be compromised through poorly secured databases or shared access.

Solutions:
- Encrypt all data in transit and at rest, using advanced algorithms and key rotation policies for added protection.
- Apply access control based on data classification and restrict high-sensitivity data from being stored in shared folders.
- Deploy Data Loss Prevention (DLP) tools to monitor and block suspicious data movements across services and devices.
Identity & Access Management (IAM) Weaknesses
Weak IAM policies often result in overprivileged users, unchecked service accounts, and lack of multi-factor authentication (MFA) enforcement. Attackers frequently exploit excessive permissions or compromised credentials to gain control over cloud-hosted resources and services.
Solutions:
- Apply least privilege access to all user roles, including internal teams, contractors, and automated cloud services.
- Set up Role-Based Access Control (RBAC) to segment access by department, sensitivity, and business function.
- Enforce MFA across all accounts and audit logs regularly for unusual access patterns or privilege escalations.
Insider Threats
Not all threats come from outside; employees or contractors may accidentally or intentionally leak sensitive information or disrupt operations. Insiders often have trusted access, making detection difficult until significant damage or data loss has already occurred.
Solutions:
- Train employees regularly on security best practices and how to recognize phishing or malicious intent internally.
- Use User and Entity Behavior Analytics (UEBA) to detect deviations from typical behavior across systems and accounts.
- Limit access to high-value systems, implement account expiration policies, and enforce regular credential changes.
Lack of Visibility & Shadow IT
Shadow IT emerges when employees use unauthorized cloud services or tools without informing the IT or security teams directly. Lack of visibility leads to uncontrolled data flows, non-compliant storage, and increased exposure to unvetted third-party risks.
Solutions:
- Deploy Cloud Access Security Brokers (CASBs) to discover and control usage of unauthorized or unsanctioned cloud tools.
- Build internal guidelines around cloud usage, file sharing, and app selection with buy-in from department heads.
- Conduct monthly reviews of all integrated tools, log files, and data transfers originating from unknown services.
Compliance & Legal Risks
Regulations like GDPR, CCPA, and HIPAA impose strict rules on how cloud-stored data must be secured, processed, and retained. Failing to meet compliance standards can result in hefty fines, loss of customer trust, and long-term reputational damage.
Solutions:
- Select cloud providers with proven compliance certifications like SOC 2, ISO 27001, or HIPAA-validated offerings.
- Automate compliance reporting and mapping using dedicated tools that track controls, responsibilities, and evidence.
- Keep an updated checklist of regional and industry-specific requirements tied to each cloud platform in use.
Ransomware & Malware in the Cloud
Ransomware groups are increasingly targeting cloud workloads, encrypting data or locking accounts to demand high-value ransom payments. Traditional antivirus tools are ineffective in modern cloud-native environments where malware can spread across multiple services rapidly.
Solutions:
- Implement cloud workload protection platforms (CWPPs) to monitor processes, file access, and potential ransomware behavior.
- Perform automated, versioned backups across multiple regions and schedule regular backup recovery tests for critical data.
- Create incident response workflows specifically for ransomware scenarios to minimize downtime and potential data loss.
Vulnerable Third-Party Integrations
Cloud environments often rely on third-party integrations that introduce risks if those partners follow weaker security practices or protocols. A compromised third-party system can become a gateway for attackers to infiltrate your cloud infrastructure and data flows.
Solutions:
- Perform security assessments and vendor risk evaluations before connecting any external service to your cloud platform.
- Enforce API-level access controls and grant the minimum scope of data or privileges required for integration.
- Continuously monitor third-party activity and revoke unused or outdated connections from legacy systems.
Inadequate Incident Response Plans
Many organizations lack a cloud-specific incident response (IR) plan, leading to slow or ineffective reactions during critical security breaches. Without defined roles, alert thresholds, or recovery playbooks, security teams often scramble to contain damage after an incident occurs.
Solutions:
- Build a cloud-specific IR plan and assign clear responsibilities to internal and external response stakeholders.
- Integrate response automation with SIEM platforms, alerting tools, and cloud provider monitoring dashboards.
- Simulate attack scenarios every quarter and refine the plan based on lessons learned from drills or real-world events.
Partner with EvinceDev for Smarter Cloud Protection
The future of cloud computing demands security strategies that evolve alongside increasingly complex infrastructure and smarter cyber threats. At EvinceDev, we help organizations build secure, scalable, and compliant cloud environments tailored to their business goals and industry needs.
If you’re unsure about your current cloud posture, book a FREE Consultation with our cloud security experts to identify and resolve critical gaps. Start today—secure your cloud, protect your data, and gain peace of mind in an ever-changing digital world.